mirror of
https://github.com/ngoduykhanh/wireguard-ui
synced 2024-05-10 09:36:39 +02:00
Update readme and code comments (#272)
This commit is contained in:
parent
4b0a0d9061
commit
ea55b36a6f
142
README.md
142
README.md
|
|
@ -5,18 +5,21 @@
|
||||||
A web user interface to manage your WireGuard setup.
|
A web user interface to manage your WireGuard setup.
|
||||||
|
|
||||||
## Features
|
## Features
|
||||||
|
|
||||||
- Friendly UI
|
- Friendly UI
|
||||||
- Authentication
|
- Authentication
|
||||||
- Manage extra client information (name, email, etc)
|
- Manage extra client information (name, email, etc)
|
||||||
- Retrieve configs using QR code / file
|
- Retrieve client config using QR code / file / email
|
||||||
|
|
||||||
|
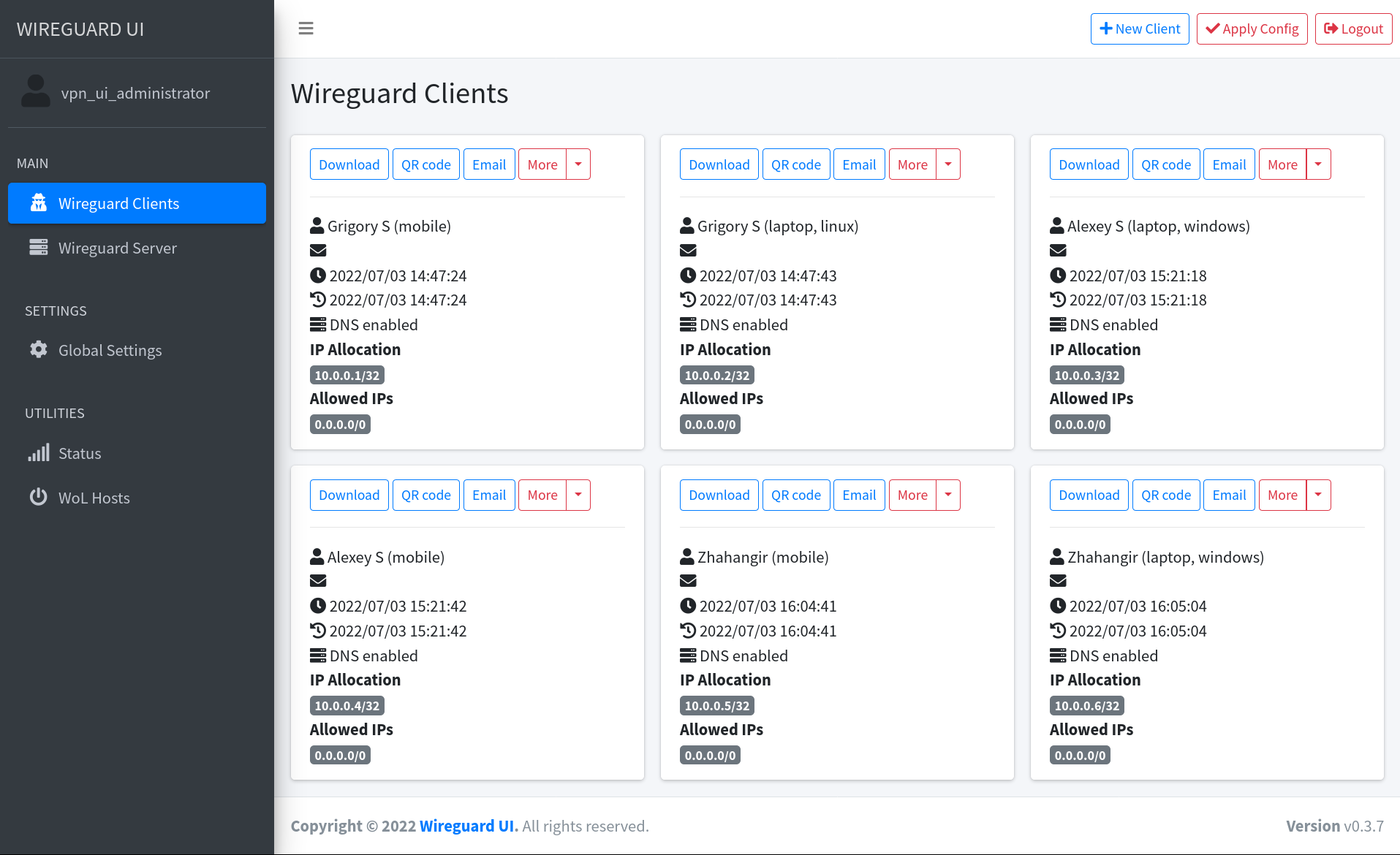
|
||||||
|
|
||||||
## Run WireGuard-UI
|
## Run WireGuard-UI
|
||||||
|
|
||||||
Default username and password are `admin`.
|
> ⚠️The default username and password are `admin`. Please change it to secure your setup.
|
||||||
|
|
||||||
### Using binary file
|
### Using binary file
|
||||||
|
|
||||||
Download the binary file from the release and run it with command:
|
Download the binary file from the release page and run it directly on the host machine
|
||||||
|
|
||||||
```
|
```
|
||||||
./wireguard-ui
|
./wireguard-ui
|
||||||
|
|
@ -24,7 +27,9 @@ Download the binary file from the release and run it with command:
|
||||||
|
|
||||||
### Using docker compose
|
### Using docker compose
|
||||||
|
|
||||||
You can take a look at this example of [docker-compose.yml](https://github.com/ngoduykhanh/wireguard-ui/blob/master/docker-compose.yaml). Please adjust volume mount points to work with your setup. Then run it like below:
|
You can take a look at this example
|
||||||
|
of [docker-compose.yml](https://github.com/ngoduykhanh/wireguard-ui/blob/master/docker-compose.yaml). Please adjust
|
||||||
|
volume mount points to work with your setup. Then run it like below:
|
||||||
|
|
||||||
```
|
```
|
||||||
docker-compose up
|
docker-compose up
|
||||||
|
|
@ -32,49 +37,60 @@ docker-compose up
|
||||||
|
|
||||||
Note:
|
Note:
|
||||||
|
|
||||||
- There is a Status option that needs docker to be able to access the network of the host in order to read the
|
- There is a Status page that needs docker to be able to access the network of the host in order to read the
|
||||||
wireguard interface stats. See the `cap_add` and `network_mode` options on the docker-compose.yaml
|
wireguard interface stats. See the `cap_add` and `network_mode` options on the docker-compose.yaml
|
||||||
- Similarly the `WGUI_MANAGE_START` and `WGUI_MANAGE_RESTART` settings need the same access, in order to restart the wireguard interface.
|
- Similarly, the `WGUI_MANAGE_START` and `WGUI_MANAGE_RESTART` settings need the same access, in order to restart the
|
||||||
- Because the `network_mode` is set to `host`, we don't need to specify the exposed ports. The app will listen on port `5000` by default.
|
wireguard interface.
|
||||||
|
- Because the `network_mode` is set to `host`, we don't need to specify the exposed ports. The app will listen on
|
||||||
|
port `5000` by default.
|
||||||
|
|
||||||
## Environment Variables
|
## Environment Variables
|
||||||
|
|
||||||
| Variable | Description |
|
| Variable | Description | Default |
|
||||||
|-----------------------------|-----------------------------------------------------------------------------------------------------------------|
|
|-----------------------------|--------------------------------------------------------------------------------------------------------------------------------------------------------------|------------------------------------|
|
||||||
| `SESSION_SECRET` | Used to encrypt the session cookies. Set this to a random value. |
|
| `BASE_PATH` | Set this variable if you run wireguard-ui under a subpath of your reverse proxy virtual host (e.g. /wireguard)) | N/A |
|
||||||
| `WGUI_USERNAME` | The username for the login page. (default `admin`) |
|
| `SESSION_SECRET` | The secret key used to encrypt the session cookies. Set this to a random value. | N/A |
|
||||||
| `WGUI_PASSWORD` | The password for the user on the login page. Will be hashed automatically. (default `admin`) |
|
| `WGUI_USERNAME` | The username for the login page | `admin` |
|
||||||
| `WGUI_PASSWORD_HASH` | The password hash for the user on the login page. (alternative to `WGUI_PASSWORD`) |
|
| `WGUI_PASSWORD` | The password for the user on the login page. Will be hashed automatically | `admin` |
|
||||||
| `WGUI_ENDPOINT_ADDRESS` | The default endpoint address used in global settings. (default is your public IP address) |
|
| `WGUI_PASSWORD_HASH` | The password hash for the user on the login page. (alternative to `WGUI_PASSWORD`) | N/A |
|
||||||
| `WGUI_DNS` | The default DNS servers (comma-separated-list) used in the global settings. (default `1.1.1.1`) |
|
| `WGUI_ENDPOINT_ADDRESS` | The default endpoint address used in global settings | Resolved to your public ip address |
|
||||||
| `WGUI_MTU` | The default MTU used in global settings. (default `1450`) |
|
| `WGUI_DNS` | The default DNS servers (comma-separated-list) used in the global settings | `1.1.1.1` |
|
||||||
| `WGUI_PERSISTENT_KEEPALIVE` | The default persistent keepalive for WireGuard in global settings. (default `15`) |
|
| `WGUI_MTU` | The default MTU used in global settings | `1450` |
|
||||||
| `WGUI_FORWARD_MARK` | The default WireGuard forward mark. (default `0xca6c`) |
|
| `WGUI_PERSISTENT_KEEPALIVE` | The default persistent keepalive for WireGuard in global settings | `15` |
|
||||||
| `WGUI_CONFIG_FILE_PATH` | The default WireGuard config file path used in global settings. (default `/etc/wireguard/wg0.conf`) |
|
| `WGUI_FORWARD_MARK` | The default WireGuard forward mark | `0xca6c` |
|
||||||
| `BASE_PATH` | Set this variable if you run wireguard-ui under a subpath of your reverse proxy virtual host (e.g. /wireguard)) |
|
| `WGUI_CONFIG_FILE_PATH` | The default WireGuard config file path used in global settings | `/etc/wireguard/wg0.conf` |
|
||||||
|
| `WG_CONF_TEMPLATE` | The custom `wg.conf` config file template. Please refer to our [default template](https://github.com/ngoduykhanh/wireguard-ui/blob/master/templates/wg.conf) | N/A |
|
||||||
|
| `EMAIL_FROM_ADDRESS` | The sender email address | N/A |
|
||||||
|
| `EMAIL_FROM_NAME` | The sender name | `WireGuard UI` |
|
||||||
|
| `SENDGRID_API_KEY` | The SendGrid api key | N/A |
|
||||||
|
| `SMTP_HOSTNAME` | The SMTP IP address or hostname | `127.0.0.1` |
|
||||||
|
| `SMTP_PORT` | The SMTP port | `25` |
|
||||||
|
| `SMTP_USERNAME` | The SMTP username | N/A |
|
||||||
|
| `SMTP_PASSWORD` | The SMTP user password | N/A |
|
||||||
|
| `SMTP_AUTH_TYPE` | The SMTP authentication type. Possible values: `PLAIN`, `LOGIN`, `NONE` | `NONE` |
|
||||||
|
| `SMTP_ENCRYPTION` | the encryption method. Possible values: `SSL`, `SSLTLS`, `TLS`, `STARTTLS` | `STARTTLS` |
|
||||||
|
|
||||||
### Defaults for server configuration
|
### Defaults for server configuration
|
||||||
|
|
||||||
These environment variables are used to control the default server settings used when initializing the database.
|
These environment variables are used to control the default server settings used when initializing the database.
|
||||||
|
|
||||||
| Variable | Description |
|
| Variable | Description | Default |
|
||||||
|-----------------------------------|--------------------------------------------------------------------------------------------------------------------------|
|
|-----------------------------------|-----------------------------------------------------------------------------------------------|-----------------|
|
||||||
| `WGUI_SERVER_INTERFACE_ADDRESSES` | The default interface addresses (comma-separated-list) for the WireGuard server configuration. (default `10.252.1.0/24`) |
|
| `WGUI_SERVER_INTERFACE_ADDRESSES` | The default interface addresses (comma-separated-list) for the WireGuard server configuration | `10.252.1.0/24` |
|
||||||
| `WGUI_SERVER_LISTEN_PORT` | The default server listen port. (default `51820`) |
|
| `WGUI_SERVER_LISTEN_PORT` | The default server listen port | `51820` |
|
||||||
| `WGUI_SERVER_POST_UP_SCRIPT` | The default server post-up script. |
|
| `WGUI_SERVER_POST_UP_SCRIPT` | The default server post-up script | N/A |
|
||||||
| `WGUI_SERVER_POST_DOWN_SCRIPT` | The default server post-down script. |
|
| `WGUI_SERVER_POST_DOWN_SCRIPT` | The default server post-down script | N/A |
|
||||||
|
|
||||||
### Defaults for new clients
|
### Defaults for new clients
|
||||||
|
|
||||||
These environment variables are used to set the defaults used in `New Client` dialog.
|
These environment variables are used to set the defaults used in `New Client` dialog.
|
||||||
|
|
||||||
| Variable | Description |
|
| Variable | Description | Default |
|
||||||
|---------------------------------------------|------------------------------------------------------------------------------------------------------------------|
|
|---------------------------------------------|-------------------------------------------------------------------------------------------------|-------------|
|
||||||
| `WGUI_DEFAULT_CLIENT_ALLOWED_IPS` | Comma-separated-list of CIDRs for the `Allowed IPs` field. (default `0.0.0.0/0`) |
|
| `WGUI_DEFAULT_CLIENT_ALLOWED_IPS` | Comma-separated-list of CIDRs for the `Allowed IPs` field. (default ) | `0.0.0.0/0` |
|
||||||
| `WGUI_DEFAULT_CLIENT_EXTRA_ALLOWED_IPS` | Comma-separated-list of CIDRs for the `Extra Allowed IPs` field. (default empty) |
|
| `WGUI_DEFAULT_CLIENT_EXTRA_ALLOWED_IPS` | Comma-separated-list of CIDRs for the `Extra Allowed IPs` field. (default empty) | N/A |
|
||||||
| `WGUI_DEFAULT_CLIENT_USE_SERVER_DNS` | Boolean value [`0`, `f`, `F`, `false`, `False`, `FALSE`, `1`, `t`, `T`, `true`, `True`, `TRUE`] (default `true`) |
|
| `WGUI_DEFAULT_CLIENT_USE_SERVER_DNS` | Boolean value [`0`, `f`, `F`, `false`, `False`, `FALSE`, `1`, `t`, `T`, `true`, `True`, `TRUE`] | `true` |
|
||||||
| `WGUI_DEFAULT_CLIENT_ENABLE_AFTER_CREATION` | Boolean value [`0`, `f`, `F`, `false`, `False`, `FALSE`, `1`, `t`, `T`, `true`, `True`, `TRUE`] (default `true`) |
|
| `WGUI_DEFAULT_CLIENT_ENABLE_AFTER_CREATION` | Boolean value [`0`, `f`, `F`, `false`, `False`, `FALSE`, `1`, `t`, `T`, `true`, `True`, `TRUE`] | `true` |
|
||||||
|
|
||||||
### Docker only
|
### Docker only
|
||||||
|
|
||||||
|
|
@ -85,37 +101,12 @@ These environment variables only apply to the docker container.
|
||||||
| `WGUI_MANAGE_START` | Start/stop WireGaurd when the container is started/stopped. (default `false`) |
|
| `WGUI_MANAGE_START` | Start/stop WireGaurd when the container is started/stopped. (default `false`) |
|
||||||
| `WGUI_MANAGE_RESTART` | Auto restart WireGuard when we Apply Config changes in the UI. (default `false`) |
|
| `WGUI_MANAGE_RESTART` | Auto restart WireGuard when we Apply Config changes in the UI. (default `false`) |
|
||||||
|
|
||||||
### Email configuration
|
|
||||||
|
|
||||||
To use a custom `wg.conf` template, set the `WG_CONF_TEMPLATE` environment variable to a path to such file. To make sure `wireguard-ui` will be able to work with it - refer to the [default template](templates/wg.conf).
|
|
||||||
|
|
||||||
In order to send the wireguard configuration to clients via email, set the following environment variables:
|
|
||||||
|
|
||||||
- using SendGrid API
|
|
||||||
|
|
||||||
```
|
|
||||||
SENDGRID_API_KEY: Your sendgrid api key
|
|
||||||
EMAIL_FROM_ADDRESS: the email address you registered on sendgrid
|
|
||||||
EMAIL_FROM_NAME: the sender's email address
|
|
||||||
```
|
|
||||||
|
|
||||||
- using SMTP
|
|
||||||
|
|
||||||
```
|
|
||||||
SMTP_HOSTNAME: The SMTP ip address or hostname
|
|
||||||
SMTP_PORT: the SMTP port
|
|
||||||
SMTP_USERNAME: the SMTP username to authenticate
|
|
||||||
SMTP_PASSWORD: the SMTP user password
|
|
||||||
SMTP_AUTH_TYPE: the authentication type. Possible values: PLAIN, LOGIN, NONE
|
|
||||||
SMTP_ENCRYPTION: the encryption method. Possible values: SSL, SSLTLS, TLS or STARTTLS (default)
|
|
||||||
EMAIL_FROM_ADDRESS: the sender's email address
|
|
||||||
EMAIL_FROM_NAME: the sender's name
|
|
||||||
```
|
|
||||||
|
|
||||||
## Auto restart WireGuard daemon
|
## Auto restart WireGuard daemon
|
||||||
WireGuard-UI only takes care of configuration generation. You can use systemd to watch for the changes and restart the service. Following is an example:
|
|
||||||
|
|
||||||
### systemd
|
WireGuard-UI only takes care of configuration generation. You can use systemd to watch for the changes and restart the
|
||||||
|
service. Following is an example:
|
||||||
|
|
||||||
|
### Using systemd
|
||||||
|
|
||||||
Create `/etc/systemd/system/wgui.service`
|
Create `/etc/systemd/system/wgui.service`
|
||||||
|
|
||||||
|
|
@ -156,12 +147,12 @@ Apply it
|
||||||
```sh
|
```sh
|
||||||
systemctl enable wgui.{path,service}
|
systemctl enable wgui.{path,service}
|
||||||
systemctl start wgui.{path,service}
|
systemctl start wgui.{path,service}
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
### openrc
|
### Using openrc
|
||||||
|
|
||||||
Create and `chmod +x` /usr/local/bin/wgui
|
Create and `chmod +x` /usr/local/bin/wgui
|
||||||
|
|
||||||
```sh
|
```sh
|
||||||
cd /usr/local/bin/
|
cd /usr/local/bin/
|
||||||
cat << EOF > wgui
|
cat << EOF > wgui
|
||||||
|
|
@ -170,10 +161,10 @@ wg-quick down wg0
|
||||||
wg-quick up wg0
|
wg-quick up wg0
|
||||||
EOF
|
EOF
|
||||||
chmod +x wgui
|
chmod +x wgui
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Create and `chmod +x` /etc/init.d/wgui
|
Create and `chmod +x` /etc/init.d/wgui
|
||||||
|
|
||||||
```sh
|
```sh
|
||||||
cd /etc/init.d/
|
cd /etc/init.d/
|
||||||
cat << EOF > wgui
|
cat << EOF > wgui
|
||||||
|
|
@ -185,7 +176,6 @@ pidfile=/run/${RC_SVCNAME}.pid
|
||||||
command_background=yes
|
command_background=yes
|
||||||
EOF
|
EOF
|
||||||
chmod +x wgui
|
chmod +x wgui
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Apply it
|
Apply it
|
||||||
|
|
@ -193,14 +183,15 @@ Apply it
|
||||||
```sh
|
```sh
|
||||||
rc-service wgui start
|
rc-service wgui start
|
||||||
rc-update add wgui default
|
rc-update add wgui default
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
### docker
|
### Using Docker
|
||||||
|
|
||||||
Set `WGUI_MANAGE_RESTART=true` to manage Wireguard interface restarts.
|
Set `WGUI_MANAGE_RESTART=true` to manage Wireguard interface restarts.
|
||||||
Using `WGUI_MANAGE_START=true` can also replace the function of `wg-quick@wg0` service, to start Wireguard at boot, by running the container with `restart: unless-stopped`.
|
Using `WGUI_MANAGE_START=true` can also replace the function of `wg-quick@wg0` service, to start Wireguard at boot, by
|
||||||
These settings can also pick up changes to Wireguard Config File Path, after restarting the container.
|
running the container with `restart: unless-stopped`. These settings can also pick up changes to Wireguard Config File
|
||||||
|
Path, after restarting the container. Please make sure you have `--cap-add=NET_ADMIN` in your container config to make this
|
||||||
|
feature work.
|
||||||
|
|
||||||
## Build
|
## Build
|
||||||
|
|
||||||
|
|
@ -210,7 +201,6 @@ Go to the project root directory and run the following command:
|
||||||
|
|
||||||
```sh
|
```sh
|
||||||
docker build -t wireguard-ui .
|
docker build -t wireguard-ui .
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
### Build binary file
|
### Build binary file
|
||||||
|
|
@ -219,7 +209,6 @@ Prepare the assets directory
|
||||||
|
|
||||||
```sh
|
```sh
|
||||||
./prepare_assets.sh
|
./prepare_assets.sh
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Then you can embed resources by generating Go source code
|
Then you can embed resources by generating Go source code
|
||||||
|
|
@ -227,7 +216,6 @@ Then you can embed resources by generating Go source code
|
||||||
```sh
|
```sh
|
||||||
rice embed-go
|
rice embed-go
|
||||||
go build -o wireguard-ui
|
go build -o wireguard-ui
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Or, append resources to executable as zip file
|
Or, append resources to executable as zip file
|
||||||
|
|
@ -235,16 +223,14 @@ Or, append resources to executable as zip file
|
||||||
```sh
|
```sh
|
||||||
go build -o wireguard-ui
|
go build -o wireguard-ui
|
||||||
rice append --exec wireguard-ui
|
rice append --exec wireguard-ui
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|
||||||
## Screenshot
|
|
||||||

|
|
||||||
|
|
||||||
## License
|
## License
|
||||||
|
|
||||||
MIT. See [LICENSE](https://github.com/ngoduykhanh/wireguard-ui/blob/master/LICENSE).
|
MIT. See [LICENSE](https://github.com/ngoduykhanh/wireguard-ui/blob/master/LICENSE).
|
||||||
|
|
||||||
## Support
|
## Support
|
||||||
|
|
||||||
If you like the project and want to support it, you can *buy me a coffee* ☕
|
If you like the project and want to support it, you can *buy me a coffee* ☕
|
||||||
|
|
||||||
<a href="https://www.buymeacoffee.com/khanhngo" target="_blank"><img src="https://cdn.buymeacoffee.com/buttons/default-orange.png" alt="Buy Me A Coffee" height="41" width="174"></a>
|
<a href="https://www.buymeacoffee.com/khanhngo" target="_blank"><img src="https://cdn.buymeacoffee.com/buttons/default-orange.png" alt="Buy Me A Coffee" height="41" width="174"></a>
|
||||||
|
|
|
||||||
|
|
@ -256,7 +256,7 @@ func NewClient(db store.IStore) echo.HandlerFunc {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
// EmailClient handler to sent the configuration via email
|
// EmailClient handler to send the configuration via email
|
||||||
func EmailClient(db store.IStore, mailer emailer.Emailer, emailSubject, emailContent string) echo.HandlerFunc {
|
func EmailClient(db store.IStore, mailer emailer.Emailer, emailSubject, emailContent string) echo.HandlerFunc {
|
||||||
type clientIdEmailPayload struct {
|
type clientIdEmailPayload struct {
|
||||||
ID string `json:"id"`
|
ID string `json:"id"`
|
||||||
|
|
@ -285,17 +285,17 @@ func EmailClient(db store.IStore, mailer emailer.Emailer, emailSubject, emailCon
|
||||||
globalSettings, _ := db.GetGlobalSettings()
|
globalSettings, _ := db.GetGlobalSettings()
|
||||||
config := util.BuildClientConfig(*clientData.Client, server, globalSettings)
|
config := util.BuildClientConfig(*clientData.Client, server, globalSettings)
|
||||||
|
|
||||||
cfg_att := emailer.Attachment{"wg0.conf", []byte(config)}
|
cfgAtt := emailer.Attachment{"wg0.conf", []byte(config)}
|
||||||
var attachments []emailer.Attachment
|
var attachments []emailer.Attachment
|
||||||
if clientData.Client.PrivateKey != "" {
|
if clientData.Client.PrivateKey != "" {
|
||||||
qrdata, err := base64.StdEncoding.DecodeString(strings.TrimPrefix(clientData.QRCode, "data:image/png;base64,"))
|
qrdata, err := base64.StdEncoding.DecodeString(strings.TrimPrefix(clientData.QRCode, "data:image/png;base64,"))
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return c.JSON(http.StatusInternalServerError, jsonHTTPResponse{false, "decoding: " + err.Error()})
|
return c.JSON(http.StatusInternalServerError, jsonHTTPResponse{false, "decoding: " + err.Error()})
|
||||||
}
|
}
|
||||||
qr_att := emailer.Attachment{"wg.png", qrdata}
|
qrAtt := emailer.Attachment{"wg.png", qrdata}
|
||||||
attachments = []emailer.Attachment{cfg_att, qr_att}
|
attachments = []emailer.Attachment{cfgAtt, qrAtt}
|
||||||
} else {
|
} else {
|
||||||
attachments = []emailer.Attachment{cfg_att}
|
attachments = []emailer.Attachment{cfgAtt}
|
||||||
}
|
}
|
||||||
err = mailer.Send(
|
err = mailer.Send(
|
||||||
clientData.Client.Name,
|
clientData.Client.Name,
|
||||||
|
|
@ -385,12 +385,12 @@ func SetClientStatus(db store.IStore) echo.HandlerFunc {
|
||||||
clientID := data["id"].(string)
|
clientID := data["id"].(string)
|
||||||
status := data["status"].(bool)
|
status := data["status"].(bool)
|
||||||
|
|
||||||
clientdata, err := db.GetClientByID(clientID, model.QRCodeSettings{Enabled: false})
|
clientData, err := db.GetClientByID(clientID, model.QRCodeSettings{Enabled: false})
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return c.JSON(http.StatusNotFound, jsonHTTPResponse{false, err.Error()})
|
return c.JSON(http.StatusNotFound, jsonHTTPResponse{false, err.Error()})
|
||||||
}
|
}
|
||||||
|
|
||||||
client := *clientdata.Client
|
client := *clientData.Client
|
||||||
|
|
||||||
client.Enabled = status
|
client.Enabled = status
|
||||||
if err := db.SaveClient(client); err != nil {
|
if err := db.SaveClient(client); err != nil {
|
||||||
|
|
@ -558,7 +558,7 @@ func Status(db store.IStore) echo.HandlerFunc {
|
||||||
}
|
}
|
||||||
return func(c echo.Context) error {
|
return func(c echo.Context) error {
|
||||||
|
|
||||||
wgclient, err := wgctrl.New()
|
wgClient, err := wgctrl.New()
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return c.Render(http.StatusInternalServerError, "status.html", map[string]interface{}{
|
return c.Render(http.StatusInternalServerError, "status.html", map[string]interface{}{
|
||||||
"baseData": model.BaseData{Active: "status", CurrentUser: currentUser(c)},
|
"baseData": model.BaseData{Active: "status", CurrentUser: currentUser(c)},
|
||||||
|
|
@ -567,7 +567,7 @@ func Status(db store.IStore) echo.HandlerFunc {
|
||||||
})
|
})
|
||||||
}
|
}
|
||||||
|
|
||||||
devices, err := wgclient.Devices()
|
devices, err := wgClient.Devices()
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return c.Render(http.StatusInternalServerError, "status.html", map[string]interface{}{
|
return c.Render(http.StatusInternalServerError, "status.html", map[string]interface{}{
|
||||||
"baseData": model.BaseData{Active: "status", CurrentUser: currentUser(c)},
|
"baseData": model.BaseData{Active: "status", CurrentUser: currentUser(c)},
|
||||||
|
|
|
||||||
4
main.go
4
main.go
|
|
@ -31,7 +31,7 @@ var (
|
||||||
flagSmtpPort int = 25
|
flagSmtpPort int = 25
|
||||||
flagSmtpUsername string
|
flagSmtpUsername string
|
||||||
flagSmtpPassword string
|
flagSmtpPassword string
|
||||||
flagSmtpAuthType string = "None"
|
flagSmtpAuthType string = "NONE"
|
||||||
flagSmtpNoTLSCheck bool = false
|
flagSmtpNoTLSCheck bool = false
|
||||||
flagSmtpEncryption string = "STARTTLS"
|
flagSmtpEncryption string = "STARTTLS"
|
||||||
flagSendgridApiKey string
|
flagSendgridApiKey string
|
||||||
|
|
@ -62,7 +62,7 @@ func init() {
|
||||||
flag.StringVar(&flagSmtpPassword, "smtp-password", util.LookupEnvOrString("SMTP_PASSWORD", flagSmtpPassword), "SMTP Password")
|
flag.StringVar(&flagSmtpPassword, "smtp-password", util.LookupEnvOrString("SMTP_PASSWORD", flagSmtpPassword), "SMTP Password")
|
||||||
flag.BoolVar(&flagSmtpNoTLSCheck, "smtp-no-tls-check", util.LookupEnvOrBool("SMTP_NO_TLS_CHECK", flagSmtpNoTLSCheck), "Disable TLS verification for SMTP. This is potentially dangerous.")
|
flag.BoolVar(&flagSmtpNoTLSCheck, "smtp-no-tls-check", util.LookupEnvOrBool("SMTP_NO_TLS_CHECK", flagSmtpNoTLSCheck), "Disable TLS verification for SMTP. This is potentially dangerous.")
|
||||||
flag.StringVar(&flagSmtpEncryption, "smtp-encryption", util.LookupEnvOrString("SMTP_ENCRYPTION", flagSmtpEncryption), "SMTP Encryption : SSL, SSLTLS, TLS or STARTTLS (by default)")
|
flag.StringVar(&flagSmtpEncryption, "smtp-encryption", util.LookupEnvOrString("SMTP_ENCRYPTION", flagSmtpEncryption), "SMTP Encryption : SSL, SSLTLS, TLS or STARTTLS (by default)")
|
||||||
flag.StringVar(&flagSmtpAuthType, "smtp-auth-type", util.LookupEnvOrString("SMTP_AUTH_TYPE", flagSmtpAuthType), "SMTP Auth Type : Plain, Login or None.")
|
flag.StringVar(&flagSmtpAuthType, "smtp-auth-type", util.LookupEnvOrString("SMTP_AUTH_TYPE", flagSmtpAuthType), "SMTP Auth Type : PLAIN, LOGIN or NONE.")
|
||||||
flag.StringVar(&flagSendgridApiKey, "sendgrid-api-key", util.LookupEnvOrString("SENDGRID_API_KEY", flagSendgridApiKey), "Your sendgrid api key.")
|
flag.StringVar(&flagSendgridApiKey, "sendgrid-api-key", util.LookupEnvOrString("SENDGRID_API_KEY", flagSendgridApiKey), "Your sendgrid api key.")
|
||||||
flag.StringVar(&flagEmailFrom, "email-from", util.LookupEnvOrString("EMAIL_FROM_ADDRESS", flagEmailFrom), "'From' email address.")
|
flag.StringVar(&flagEmailFrom, "email-from", util.LookupEnvOrString("EMAIL_FROM_ADDRESS", flagEmailFrom), "'From' email address.")
|
||||||
flag.StringVar(&flagEmailFromName, "email-from-name", util.LookupEnvOrString("EMAIL_FROM_NAME", flagEmailFromName), "'From' email name.")
|
flag.StringVar(&flagEmailFromName, "email-from-name", util.LookupEnvOrString("EMAIL_FROM_NAME", flagEmailFromName), "'From' email name.")
|
||||||
|
|
|
||||||
|
|
@ -1,6 +1,6 @@
|
||||||
package model
|
package model
|
||||||
|
|
||||||
// Defaults for creation of new clients used in the templates
|
// ClientDefaults Defaults for creation of new clients used in the templates
|
||||||
type ClientDefaults struct {
|
type ClientDefaults struct {
|
||||||
AllowedIps []string
|
AllowedIps []string
|
||||||
ExtraAllowedIps []string
|
ExtraAllowedIps []string
|
||||||
|
|
|
||||||
|
|
@ -16,8 +16,6 @@ var (
|
||||||
SendgridApiKey string
|
SendgridApiKey string
|
||||||
EmailFrom string
|
EmailFrom string
|
||||||
EmailFromName string
|
EmailFromName string
|
||||||
EmailSubject string
|
|
||||||
EmailContent string
|
|
||||||
SessionSecret []byte
|
SessionSecret []byte
|
||||||
WgConfTemplate string
|
WgConfTemplate string
|
||||||
BasePath string
|
BasePath string
|
||||||
|
|
|
||||||
14
util/util.go
14
util/util.go
|
|
@ -82,15 +82,15 @@ func BuildClientConfig(client model.Client, server model.Server, setting model.G
|
||||||
return strConfig
|
return strConfig
|
||||||
}
|
}
|
||||||
|
|
||||||
// Read the default values for creating a new client from the environment or use sane defaults
|
// ClientDefaultsFromEnv to read the default values for creating a new client from the environment or use sane defaults
|
||||||
func ClientDefaultsFromEnv() model.ClientDefaults {
|
func ClientDefaultsFromEnv() model.ClientDefaults {
|
||||||
client_defaults := model.ClientDefaults{}
|
clientDefaults := model.ClientDefaults{}
|
||||||
client_defaults.AllowedIps = LookupEnvOrStrings(DefaultClientAllowedIpsEnvVar, []string{"0.0.0.0/0"})
|
clientDefaults.AllowedIps = LookupEnvOrStrings(DefaultClientAllowedIpsEnvVar, []string{"0.0.0.0/0"})
|
||||||
client_defaults.ExtraAllowedIps = LookupEnvOrStrings(DefaultClientExtraAllowedIpsEnvVar, []string{})
|
clientDefaults.ExtraAllowedIps = LookupEnvOrStrings(DefaultClientExtraAllowedIpsEnvVar, []string{})
|
||||||
client_defaults.UseServerDNS = LookupEnvOrBool(DefaultClientUseServerDNSEnvVar, true)
|
clientDefaults.UseServerDNS = LookupEnvOrBool(DefaultClientUseServerDNSEnvVar, true)
|
||||||
client_defaults.EnableAfterCreation = LookupEnvOrBool(DefaultClientEnableAfterCreationEnvVar, true)
|
clientDefaults.EnableAfterCreation = LookupEnvOrBool(DefaultClientEnableAfterCreationEnvVar, true)
|
||||||
|
|
||||||
return client_defaults
|
return clientDefaults
|
||||||
}
|
}
|
||||||
|
|
||||||
// ValidateCIDR to validate a network CIDR
|
// ValidateCIDR to validate a network CIDR
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue